Protect What Matters To You With Our Cyber Security Services
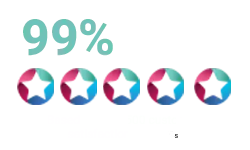
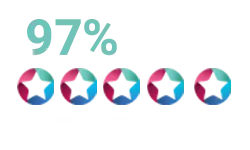
1/3 of UK businesses have experienced a cyber breach in the last 12 months.
With cyber-attacks becoming increasingly more sophisticated, it’s really important to stay ahead when it comes to your cyber security, but how? We’ll protect your business from the inside-out against sophisticated cyber threats, so you can focus on running your business.